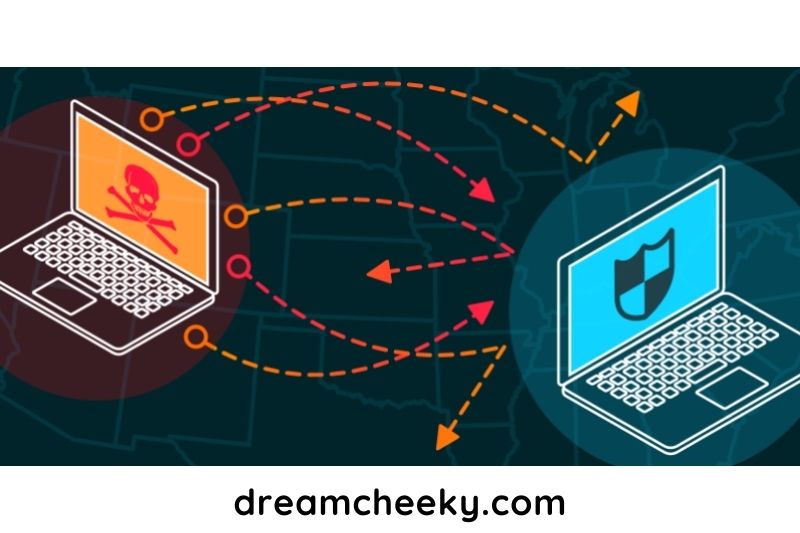
In this article, Dreamcheeky will be discussing how to DDoS on Xbox. While the process of DDoSing an Xbox is not as simple as on other platforms, it can be done with the right tools and knowledge. Keep reading to get detailed information.
What Is A DDoS Attack?
- GAME PASS ULTIMATE: Jump into the world of Xbox with everything you need to play, including an Xbox Series S and hundreds of high-quality games with 3 months of Game Pass Ultimate.*
- IN THE BOX: Bundle includes: Xbox Series S console, 3 month Xbox Game Pass Ultimate membership, one Xbox Wireless Controller, a high-speed HDMI cable, power cable, and 2 AA batteries.
- XBOX SERIES S: Experience the best value in gaming with Xbox Series S, featuring a 512GB custom SSD.
- Make the most of every gaming minute with Quick Resume, lightning-fast load times, and gameplay of up to 120 FPS—all powered by Xbox Velocity Architecture
- Be the first to play new games like Starfield and Forza Motorsport on day one with the included 3 months of Game Pass Ultimate. Plus, enjoy hundreds of other high-quality games like Minecraft Legends, Halo Infinite, and Forza Horizon 5.
- XBOX SERIES X: The fastest, most powerful Xbox ever. Explore rich new worlds with 12 teraflops of raw graphic processing power, DirectX ray tracing, a custom SSD, and 4K gaming.*
- FASTER LOAD TIMES: Make the most of every gaming minute with Quick Resume, lightning-fast load times, and gameplay of up to 120 FPS – all powered by Xbox Velocity Architecture.
- IN THE BOX: Xbox Series X console, one Xbox Wireless Controller, an ultra high-speed HDMI cable, power cable, and 2 AA batteries.
- SURROUND SOUND: Enhance gameplay with both full-spectrum visuals and immersive audio with Dolby Vision and Dolby Atmos
- XBOX GIFT CARD: Buy full digital game downloads, game add-ons, in-game currency, memberships, devices, apps, movies, TV shows, and more.
- DIGITAL GAMES: Choose from hundreds of games, from AAA to indie options. Start playing the moment your most anticipated game is available when you pre-order and pre-download it.
- GAME AD-ONS: Extend the experience of your favorite games with add-ons and in-game currency.
- MOVIES & TV SHOWS: Rent or buy new and popular movies and TV shows from a massive library.
- PERFECT GIFT: Great as a gift for a friend or yourself. Xbox Gift Cards are easy to use, never expire, and give the freedom to pick the gift they want. Enjoy more ways to play without a credit card attached to your Microsoft account.
- Microsoft Xbox One X 1TB Console with Wireless Controller: Xbox One X Enhanced, HDR, Native 4K, Ultra HD
- Games play better on Xbox One X With 40% more power than any other console, experience immersive true 4K gaming. Watch 4K Blu-ray movies; stream 4K video on Netflix, Amazon, and YouTube, among others; and listen to music with Spotify.
- Connect and play with friends and family on Xbox Live, the fastest, most reliable gaming network Find friends, rivals and teammates in the best global gaming community. Xbox Live is the most advanced multiplayer network and provides steady gameplay and fast downloads. Compete, connect, and share across platforms with gamers on Xbox One and Windows 10. Get two-four free games each month with Xbox Live Gold.
- Get exclusive offers like unlimited access to over 100 games to start playing right away Xbox Game Pass gives you instant, unlimited access to over 100 highly-rated and fun games, with new games being added all the time.
- Experience hundreds of legendary games from all Xbox consoles with backward compatibility. Enjoy the freedom of Xbox Play Anywhere games on both Xbox One and Windows 10 PC at no additional cost.
- Processor Manufacturer: AMD
- Processor Type: Zen 2
- Processor Core: Octa-core (8 Core)
- Processor Speed: 3.80 GHz
- Standard Memory: 16 GB
- Processor Manufacturer: AMD
- Processor Type: Zen 2
- Processor Core: Octa-core (8 Core)
- Processor Speed: 3.60 GHz
- Standard Memory: 10 GB
- Note: Kinect sensor sold seperately.Check the CD format and file type Supported formats include: CD-DA CD-ROM CD-ROM XA CD-R, CD-RW CD-Extra.
- Supported file types include: WMA MP3 JPEG
- This item includes the Xbox One console, 1 wireless controller, HDMI cable, and power supply . For more troubleshooting steps please check the manufacturer's webiste
- Play games like Titanfall and Halo on a network powered by over 300,000 servers for maximum performance.
- Troubleshooting Steps: If the Xbox does not play the game or It turns on but screen goes black : Please power cycle the unit by unplugging it from the wall, waiting 10 seconds and plugging it back in and power on the device.
- Memory storage capacity, 500.0
DDoS attacks are an enhanced version of Distributed Denial of Service attacks. To flood a target, a DoS attack only uses one machine. DDoS attacks multiply the attack by hundreds or even thousands. How does this happen? The botnet is key to all DDoS attacks because it allows the attacker to command many devices.
By exploiting and infecting devices, a botnet can be formed. This could be any regular desktop computer or any smart device connected to the Internet of Things. These compromised devices are known as zombies and can be joined one by one until the attacker gains all of the power they need.
A zombie is an entity controlled by infection and capable of performing basic tasks. This is similar to a botnet-controlled computer zombie. The infected person can command the machine to stop functioning once it is commanded. Computers, in general, are very dumb and do what you tell them. Cybercrime activity is a prime target for computers when they have a vulnerability exploit or malware installed.
This attacker can control their botnet through a Command and Control server. This server transmits all commands to zombie machines and sends the botnet data back to the C2 via the C2.
Types of DDOS Attacks
DoS attacks can be broken down into two categories:
1. Layer 7 attacks, also known as DoS and DDoS threats, are attempts to overload servers by sending large requests requiring resource-intensive processing and handling. This category also includes HTTP floods and slow attacks (e.g., Slowloris, RUDY), as well as DNS query flood attacks.
Application layer attacks are usually measured in requests per second (RPS). Most websites of medium size can be crippled with between 50 and 100 RPS.
2. Layer 3-4 attacks, also known as network layer attacks, are DDoS attacks that attempt to block the “pipelines” between your network and it. This category includes UDP flood and SYN flood as well as NTP amplification, DNS amplification attacks, and many other attack vectors.
These can all be used to block access to your servers and cause severe operational damages such as account suspensions or massive overage fees.
DDoS attacks are often high-traffic events. They are usually measured in gigabits per sec (Gbps) and packets per sec (PPS). Although the largest network layer attacks can reach 200 Gbps, 20-40 Gbps is sufficient to shut down most networks infrastructures.
How to DDOS on Xbox
1. Get the IP Address of a player using an IP Puller
- This Certified Refurbished product is tested and certified to look and work like new. The refurbishing process includes functionality testing, basic cleaning, inspection, and repackaging. The product ships with all relevant accessories, a minimum 91-day warranty, and may arrive in a generic box. Only select sellers who maintain a high-performance bar may offer Certified Refurbished products on Amazon.com.
- Dell Optiplex 7050 SFF Desktop PC, Intel Quad Core i7-7700 up to 4.2 GHz, 32GB DDR4, 1TB SSD
- Includes: USB Keyboard & Mouse, USB WiFi adapter, USB Bluetooth adapter, Microsoft office 30 days free trail.
- USB3.0, Type-C, DisplayPort, HDMI, Headphone output, Microphone input, LAN
- Support 4K (3840x2160) Dual display, makes it easy to connect two monitors at the same time, and you can expand working Windows, mirror content, or expand a single window across multiple monitors.
- This Dell 9020 SFF desktop computer, features 4th Generation Intel Core i7-4770 upto 3.9 Ghz processor 32GB RAM, 1TB SSD
- With a small form factor design, the Dell Desktop Computer provides the workstation performance you need without taking up too much desk space
- Visuals are handled by an HD Graphics 4600 (2x Display Port 1x VGA) DisplayPort to HDMI adapter Included
- Features USB 3.0 and USB 2.0 ports for ultra-fast data transfers. USB 3.0 is up to 10 times faster than USB 2.0, yet fully compatible with USB 2.0
- Stay connected to the WiFi Adapter. Play your favorite music files with stereo sound. Easily connect to large and multiple monitors through the installed onboard video connections.
- POWERFUL PERFORMANCE: Effortlessly Tackle Any Task with the Powerful 13th Gen Intel Core i5 Processor and 16GB DDR4 Memory.
- LIMITLESS PRODUCTIVITY: Break boundaries with the versatile new Inspiron Compact Desktop.
- SEAMLESS CONNECTION: Experience the next level of connectivity with New WiFi 6, which offers faster speeds, stability and range. Eliminate the frustration of waiting for a stable connection.
- IMMERSIVE VISUALS EXPERIENCE: Expand your workspace by connecting up to three FHD monitors or one 4K monitor via the rear HDMI and Display Port connectors.
- PREMIUM SERVICES: Premium Support with SupportAssist, the smart technology that keeps your PC performing at its best.
- This Certified Refurbished product is tested and certified to look and work like new. The refurbishing process includes functionality testing, basic cleaning, inspection, and repackaging. The product ships with all relevant accessories, a minimum 90-day warranty, and may arrive in a generic box. Only select sellers who maintain a high-performance bar may offer Certified Refurbished products on Amazon.com.
- HP Elite 6200 Small Form Factor Desktop PC, Intel Quad Core i5-2400 up to 3.4GHz, 8G DDR3, 1T, DVDRW, WiFi, Windows 10 64-Multi-Language Support English/Spanish/French (Renewed)
- Includes: USB Keyboard & Mouse, WiFi Adapter, Microsoft office 30 days free trail.
- Ports: USB 2.0, DisplayPort, VGA, PS/2 keyboard, PS/2 mouse, RJ-45, microphone/headphone jack, line in, line out.
- Operating System: Windows 10 64 Bit – Multi-language supports English/Spanish/French.
- Dell 7010 Intel I5 Quad-Core 3. 2 GHz Processor
- What's Inside: 16GB RAM, 2TB Hard Drive, DVW Optical Drive,
- Operating System: Windows 10 Professional
- Includes: USB Keyboard and Mouse
- 【Premium RAM and Storage】 Enhance multitasking capabilities with 32GB RAM, while enjoying significantly faster performance compared to traditional hard drives with a 256GB PCIe M.2 SSD + 1TB Hard Disk Drive.
- 【Processor】 12th Gen Intel Core i3-12100 (up to 4.3 GHz with Intel Turbo Boost Technology, 12 MB L3 cache, 4 cores, 8 threads)
- 【Graphics and DVD】 The system includes an integrated Intel UHD 730 Graphics card and a slim drive with an emergency eject pinhole for reading from and writing to CDs and DVDs.
- 【Connectivity and Ports】 The system offers Wi-Fi 6 and Bluetooth combo for connectivity, along with a comprehensive range of ports including HDMI, VGA, RJ-45, and 8 USB ports (4 USB 2.0 and 4 USB 3.2 Gen 1).
- 【Operating System】 Optimize your computing experience with the Windows 11 Pro, 64-bit operating system, delivering a seamless user interface and language support in US English. The package also includes a , HP 125 wired USB Keyboard in Black, designed with an English (UK) layout, as well as a matching HP 125 wired USB Mouse in Black. Elevate your computing experience with this comprehensive set of accessories.
- Get a fresh perspective with Windows 11: From a rejuvenated Start menu, to new ways to connect to your favorite people, news, games, and content—Windows 11 is the place to think, express, and create in a natural way
- AMD Athlon Silver 3050U Mobile processor with Radeon graphics: Responsive performance and modern features to simplify everyday tasks
- AMD Radeon graphics: Whether it’s games or movies, experience high performance for all your entertainment
- Dual front-facing speakers: Pump up the volume to your favorite music, movie or game. When your audio is directed towards you, nothing comes between you and your entertainment
- HP Privacy Camera: The pop-up camera is only enabled when in use, securing your privacy
- ROBUST COMPUTING HUB: Tackle any task—from basic computing to multimedia entertainment—every time you power up this beastly machine. Easily expandable and driven by a 13th Gen Intel Core i5 processor, it has the speed, power and storage to do more—everyday!
- 13th Generation Intel Core i5-13400 10-Core Processor (Up to 4.6GHz) | Intel UHD Graphics 730
- 8GB 3200MHz DDR4 Memory (up to 32GB) | 512GB M.2 2280 PCIe Gen 4 SSD | Secure Digital (SD) Card Reader
- Intel Wireless Wi-Fi 6E AX211 (Gig+) supports dual-stream Wi-Fi in the 2.4GHz, 5GHz and 6GHz bands, including UL MU-MIMO | Bluetooth 5.3 | 10/100/1000 Gigabit Ethernet LAN
- 1 - USB 3.2 Gen1 5 Gbps, Type-C (Front) | 2 - USB 3.2 Gen1 5Gbps Ports (1 Front and 1 Rear) | 4 - USB 2.0 480Mbps Ports (Rear) | 1 - HDMI 1.4b Port and 1 - HDMI 2.0 Port (Rear) | 1 - Ethernet RJ-45 Port (Rear)
- 【6-Core AMD RYZEN5】AMD Ryzen 5 5600G Processor (6 Cores, 12 Threads, 3.9 GHz Base Clock Speed up to 4.4GHz Max Boost Clock Speed) for elite gaming and content creation with 7nm leading edge technology and no limitations
- 【AMD Radeon RX6400】AMD Radeon RX6400 (4GB GDDR6 dedicated memory); get all the power you need for fast, smooth, power-efficient performance with the all-new AMD Turing) architecture
- 【High Speed】With 32GB of RAM, everything from browsing multiple web pages to playing games gets a performance boost
- 【Enormous Space】Get up to 10x faster performance than a traditional hard drive with 1TB of PCIe NVMe M.2 Solid State Drive storage and 1TB HDD for more storage space
- 【Tech Specs】2 x USB 3.1 Gen 1 (front), 1 x USB 3.1 Gen 1 Type-C (front), 2 x USB 3.1 (Gen 2 Type-A), 4 x USB 2.0 (rear), 1 x HDMI, 1 x headphone/Microphone combo, 1 x DisplayPort and 10/100/1000 Base-T Network; 5.1 Surround Sound Output ports; Realtek Wi-Fi 5 (1x1) and Bluetooth 4.2 Combo, MU-MIMO supported; HP USB Black Wired keyboard and mouse combo included, Z&O HDMI Cable also included
- 【High Speed RAM And Enormous Space】16GB of DDR4 memory is designed to handle even the most demanding workloads with ease. 512GB PCIe SSD has plenty of space to store your digital photos, music library and document files
- 【Processor】Intel Core i5-10500T (12 MB Cache, 6 Cores, 12 Threads, 2.3 GHz to 3.9 GHz) with Intel UHD Graphics
- 【Tech Specs】4 x Superspeed USB Type-A, 2 x USB Type-A 2.0, 2 x Display Ports, 1 x HDMI, 1 x RJ45, 1 x Universal Audio Jack, Wired Keyboard and Mouse, Wi-Fi 5 and Bluetooth
- 【Operating System】Windows 11 Pro operating system offers powerful platform to efficiently run routine applications
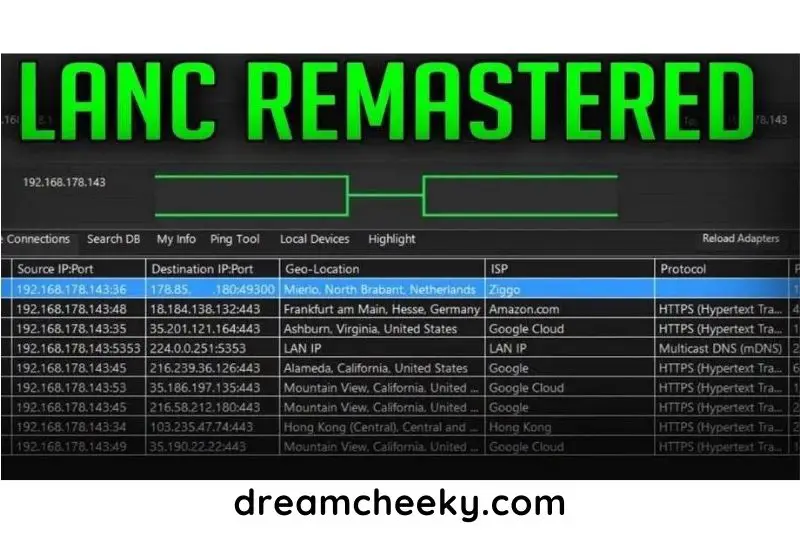
We will be using the famous Lanc Remastered software to pull IP addresses from any player. So let’s download what’s needed to start.
Requirements
- Lanc Remastered or check out our top 5 IP pullers of 2021
- Windows Pcap (if you are running Windows 10 get it here, otherwise get the default version here)
- Winrar or 7Zip to extract the files
- Microsoft Visual C++
Now, let’s start the application and fill in your Xbox details.
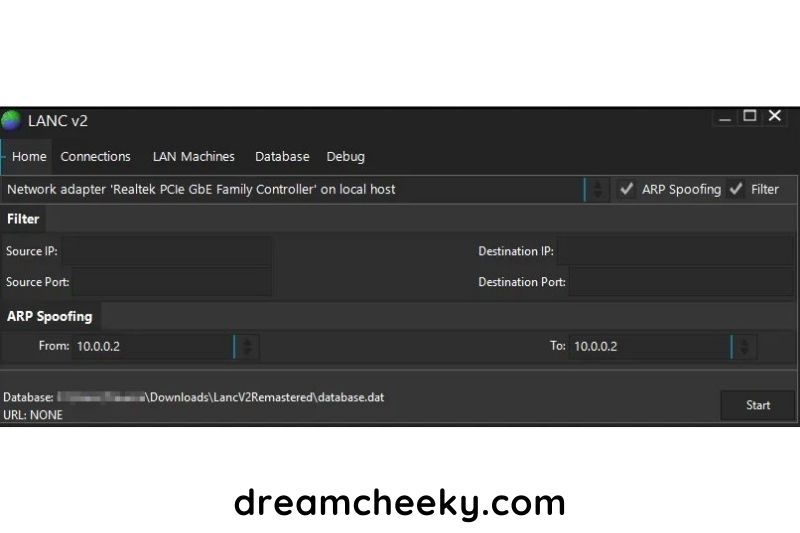
Which network adapter would you like to use? Whether you choose a wired or wireless connection, be sure to tick the box for ARP spoofing and filtering.
Now let’s get your IP onto your Xbox. On your gaming console go to settings > network settings and get the IP information. Note down your IP address and put it into the TO section under ARP Spoofing.
In the Destination Port type in the following (or leave blank if preferred)
- Xbox port 3074
Make sure you’re from address is set to your default gateway/router. This will ensure that all of your messages are sent through your router.
Create your Xbox party with other players and make sure everything is correct. Once they have joined your party, click on start to begin your gaming session.
As you explore the connections tab, you’ll see all the IP addresses connected to your port. Notice the ones that stand out, whether they have the most packets connected or not.
2. Use Xbox IP Booter
Now we can use that IP address you found to launch a DDOS attack against your chosen target.
Use any of our IP Stressers/Booters and DDOS Tools listed here and proceed with step 3.
3. Select DDOS attack Type and port number
There are several types of DDoS attacks, and we will select a network layer 4 attacks with a UDP flood.
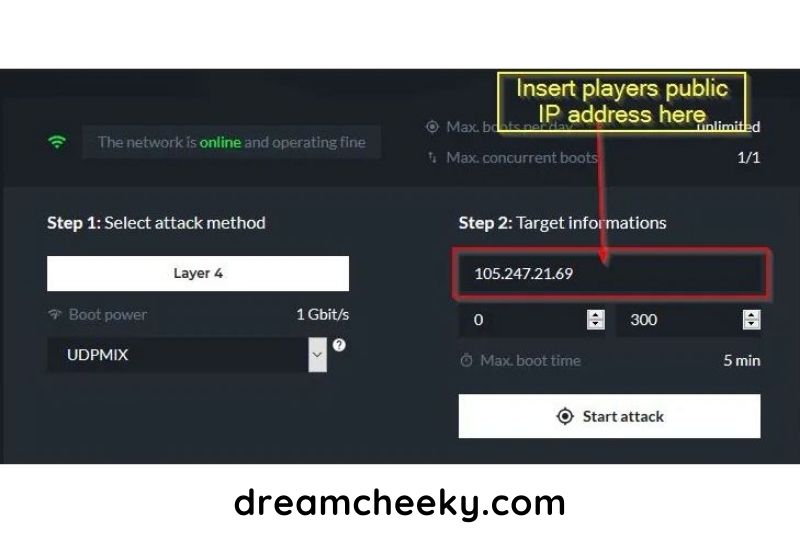
4. Target booted offline
Your target will be removed from game chat and banished to the nether realms.
Xbox DDOS vs DOS
- 🖥 POWERFUL PROCESSOR and SUPERIOR STORAGE: Configured with top of the Intel Core i5 processor for lightning-fast, reliable and consistent performance to ensure an exceptional PC experience. 16GB RAM memory to smoothly run multiple applications and browser tabs all at once. 2TB HDD storage space to store apps, games, photos, music, and movies. Loaded with 16GB to zip through multiple tasks in a hurry without lag.
- 🖥️ New 22 Inch Full HD (1920x1080) LED monitor: with 75hz, High-Quality panel with quick refresh rate and response time. With 1080p resolution, you can enjoy gaming or a modern computing experience. 22 Inch monitor has a Smart Contrast to provide optimized image quality. Bezel-less and sleek design with glossy finish, crisp edge-to-edge visuals. Wide Viewing Angles for clarity from any viewpoint. VESA Mountable and built-in tilt options allow for a variety of monitor configurations.
- ⌨️ +🖱️ RGB KEYBOARD AND MOUSE | RGB SPEAKER: 3 LED colors - Blue, red, green, Backlight LED Lights for use at night time, looks amazing. The keyboard mouse and speaker are responsive, reliable, and probably plastered in RGB lights. It's important you pick the right one for your desktop.
- 💿 WINDOWS 10 Pro LATEST: A new installation of the latest Microsoft Windows 10 Professional 64 Bit Operating System software, free of bloatware commonly installed from other manufacturers. As Microsoft's latest and best OS to date, Windows 10 Pro 64 Bit will maximize the utility of each PC for years to come. Optional software such as Anti-Virus and Office 365 can also be easily downloaded through the Microsoft Windows App Store.
- This Product is professionally inspected and tested to look and work like new. The refurbishing process includes functionality testing, basic cleaning, inspection, and repackaging. The product ships with all relevant accessories, a minimum 90-day , and may arrive in a generic box.
- RGB LIGHTS PANEL: The Dell Desktop Computer comes with RGB LED Light on front Panel. Lighting can be changed with a remote controller and quickly adjust the lighting speed, and the mode with several color changing patterns.
- PROCESSOR and STORAGE: Configured with Intel Core i5 Quad Core Processor 3.20 GHz, so you can expect reliable and consistent performance to ensure an exceptional PC experience. 16 GB RAM memory to smoothly run multiple applications and browser tabs all at once. Upgraded with 512GB SSD that can boot very fast and enough storage space to store apps, photos, music, and movies.
- OPERATING SYSTEM: With Windows 10 Pro 64-Bit Operating System software installed, this desktop computer load programs, and makes a perfect home or office computer. Optional software such as Anti-Virus and Office 368 can also be easily downloaded through the Microsoft Windows App Store.
- HAJAAN GAMING KEYBOARD, MOUSE & HEADSET: The Gaming Keyboard has 3 LED colors - Red, Green and Blue. Backlight LED Lights can be used at night time, which create a vibrant environment. The Gaming Mouse has different colors of Backlight Lights which look amazing. The Gaming Headset is extremely comfortable to wear for long gaming sessions.
- POWERFUL PROCESSOR - Configured with top of the line series processor for lightning fast, reliable and consistent performance to ensure an exceptional PC experience.
- SUPERIOR STORAGE AND MEMORY – Customized with 250GB storage space to store apps, games, photos, music and movies. Loaded with DELLGB of RAM to zip through multiple tasks in a hurry without lag.
- BUILT IN CONNECTIVITY - Stay connected to the internet with USB WIFI Adaptor. Play your favorite music files with stereo sound. Easily connect to large and multiple monitors through the installed onboard video connections.
- WINDOWS 10 LATEST RELEASE - A new installation of the latest Microsoft Windows 10 Professional 64 Bit Operating System software, free of bloatware commonly installed from other manufacturers. As Microsoft's latest and best OS to date, Windows 10 Professional 64 Bit will maximize the utility of each PC for years to come. Optional software such as Anti-Virus and Office 365 can also be easily downloaded through the Microsoft Windows App Store.
- BUY WITH CONFIDENCE - All Amazon Renewed computers come with a 90-day warranty and technical support to provide customers with unmatched quality and care.
- This computer is well-suited for a variety of tasks including gaming, study, home, business, photo and video editing, streaming, day trading, crypto trading, and more.
- This high-performance gaming PC is capable of running a wide range of popular games, including Fortnite, Call of Duty Warzone, Escape from Tarkov, GTA V, World of Warcraft, LOL, Valorant, Apex Legends, Roblox, Overwatch, CSGO, Battlefield V, Minecraft, Elden Ring, Rocket League, The Division 2, and Hogwarts Legacy with 60+ FPS
- System: Intel Core i7 up to 3.9GHz 4-Core | 16GB Memory | 512GB Solid State Drive | Genuine Windows 10 Home 64-bit
- Connectivity: 2x USB 3.0 | 6x USB 2.0 | 1x RJ-45 | 1x Serial | USB Wi-Fi | USB Bluetooth 5.0 | AMD Radeon RX 580 8G GDDR5 Video Card | 1x HDMI | 1x DisplayPort | 1x DVI
- Special feature: RGB BT Sound Bar | RGB Fan x 6 | RGB Mouse Pad | RGB Gaming Mouse & Keyboard | 1 Year parts & labor | Free lifetime tech support
- This Certified Refurbished product is tested and certified to look and work like new. The refurbishing process includes functionality testing, basic cleaning, inspection, and repackaging. The product ships with all relevant accessories, a minimum 91-day warranty, and may arrive in a generic box. Only select sellers who maintain a high-performance bar may offer Certified Refurbished products on Amazon.com.
- Dell Optiplex 7050 SFF Desktop PC, Intel Quad Core i7-7700 up to 4.2 GHz, 32GB DDR4, 1TB SSD
- Includes: USB Keyboard & Mouse, USB WiFi adapter, USB Bluetooth adapter, Microsoft office 30 days free trail.
- USB3.0, Type-C, DisplayPort, HDMI, Headphone output, Microphone input, LAN
- Support 4K (3840x2160) Dual display, makes it easy to connect two monitors at the same time, and you can expand working Windows, mirror content, or expand a single window across multiple monitors.
- This Certified Refurbishd product is tested and certified to look and work like new. The refurbishing process includes functionality testing, basic cleaning, inspection, and repackaging. The product ships with all relevant accessories, and may arrive in a generic box. Only select sellers who maintain a high performance bar may offer Certified Refurbishd products on Amazon.com
- Intel Core 2 Duo 3.0GHz Processor.
- New 4GB Memory - 160GB SATA Hard Drive.
- Windows 10 Professional 64BIT
- Keyboard, Power Cord, and Mouse included.
- System: Intel Core i5 up to 3.7GHz 4-Core | 16GB Memory | 512GB Solid State Drive | Genuine Windows 10 Home 64-bit
- Graphics: AMD Radeon RX 550 4G GDDR5 Video Card | 1x HDMI | 1x DisplayPort | 1x DVI
- Connectivity: RGB Fan x 3 | 1x RJ-45 | 1x Serial | USB Wi-Fi | USB Bluetooth 5.0
- Special feature: RGB Gaming Mouse & Keyboard | RGB Mouse Pad
- 1 Year parts & labor | Free lifetime tech support
- INTEL Core i5 13400F 2.5GHz (4.6GHz Max Boost) CPU Processor | 1TB NVME SSD – Up to 30x Faster Than Traditional HDD
- NVIDIA Geforce RTX 3050 GDDR6 Graphics Card (Brand may vary) | 16GB DDR4 RAM 3200 Gaming Memory with Heat Spreader | Windows 11 Home 64-bit
- 802.11 AC | No Bloatware | Graphic output options include 1 x HDMI, and 1 x Display Port Guaranteed, Additional Ports may vary | USB Ports Including 2.0, 3.0, and 3.2 Gen1 Ports | HD Audio and Mic | Free Gaming Keyboard and Mouse
- 4 RGB Fans for Maximum Air Flow | Skytech Nebula Black Edition with Front Mesh | 1 Year Warranty on Parts and Labor | Lifetime Free Technical Support | Assembled in the USA
- This powerful gaming PC is capable of running all your favorite games such as Call of Duty Warzone, Fortnite, Escape from Tarkov, Grand Theft Auto V, Valorant, World of Warcraft, League of Legends, Apex Legends, Roblox, PLAYERUNKNOWN's Battlegrounds, Overwatch 2, Counter-Strike 2, Battlefield V, New World, Minecraft, Elden Ring, Rocket League, Baldur's Gate 3, Dota 2, HELLDIVERS 2, Monster Hunter, Palworld, Terraria, Rainbow Six Siege, Dragon's Dogma 2, and more at Ultra settings, detailed 1080p Full HD resolution, and smooth 60 plus FPS gameplay.
- INTEL Core i5 13400F 2.5GHz (4.6GHz Max Boost) CPU Processor | 1TB NVME SSD – Up to 30x Faster Than Traditional HDD
- NVIDIA Geforce RTX 4060 8GB GDDR6X Graphics Card (Brand may vary) | 16GB DDR4 RAM 3200 Gaming Memory with Heat Spreader | Windows 11 Home 64-bit
- 802.11 AC | No Bloatware | Graphic output options include 1 x HDMI, and 1 x Display Port Guaranteed, Additional Ports may vary | USB Ports Including 2.0, 3.0, and 3.2 Gen1 Ports | HD Audio and Mic | Free Gaming Keyboard and Mouse
- 4 RGB Fans for Maximum Air Flow | Skytech Nebula Black Edition with Front Mesh | 1 Year Warranty on Parts and Labor | Lifetime Free Technical Support | Assembled in the USA
- This powerful gaming PC is capable of running all your favorite games such as Call of Duty Warzone, Fortnite, Escape from Tarkov, Grand Theft Auto V, Valorant, World of Warcraft, League of Legends, Apex Legends, Roblox, PLAYERUNKNOWN's Battlegrounds, Overwatch 2, Counter-Strike 2, Battlefield V, New World, Minecraft, Elden Ring, Rocket League, Baldur's Gate 3, Dota 2, HELLDIVERS 2, Monster Hunter, Palworld, Terraria, Rainbow Six Siege, Dragon's Dogma 2, and more at Ultra settings, detailed 1080p Full HD resolution, and smooth 60 plus FPS gameplay.
- AMD Ryzen 5 3600 3.6GHz (4.2GHz Max Boost) CPU Processor | 500GB NVME SSD – Up to 30x Faster Than Traditional HDD
- NVIDIA Geforce GTX 1650 4GB GDDR6 Graphics Card (Brand may vary) | 16GB DDR4 RAM 3200 Gaming Memory with Heat Spreader | Windows 11 Home 64-bit
- 802.11 AC | No Bloatware | Graphic output options include 1 x HDMI, and 1 x Display Port Guaranteed, Additional Ports may vary | USB Ports Including 2.0, 3.0, and 3.2 Gen1 Ports | HD Audio and Mic | Free Gaming Keyboard and Mouse
- 4 RGB Fans for Maximum Air Flow | Skytech Nebula Black Edition with Front Mesh | 1 Year Warranty on Parts and Labor | Lifetime Free Technical Support | Assembled in the USA
- This powerful gaming PC is capable of running all your favorite games such as Call of Duty Warzone, Fornite, Escape from Tarkov, Grand Theft Auto V, Valorant, World of Warcraft, League of Legends, Apex Legends, Roblox, PLAYERUNKNOWN's Battlegrounds, Overwatch, Counter-Strike: Global Offensive, Battlefield V, New World, Minecraft, Elden Ring, Rocket League, The Division 2, and more at Ultra settings, detailed 1080p Full HD resolution, and smooth 60+ FPS gameplay.
There are significant differences between distributed and regular denial-of-service attacks. A DoS attack is when a perpetrator exploits a software vulnerability to flooding a target computer with fake requests. This usually happens in an effort to exhaust server resources (e.g., RAM and CPU).
Distributed denial-of-service (DDoS), on the other hand, is launched from many connected devices distributed over the InterInternet to the sheer number of devices involved; these multi-person, multidevice attacks are often more difficult to deflect. DDoS attacks tend to attack the network infrastructure rather than single-source DoS attacks. This is to try to flood it with large volumes of traffic.
DDoS attacks can also be executed in different ways. Denial of Service attacks is generally launched with home-brewed scripts or DoS Tools (e.g., Low Orbit Ion Cannon). In contrast, DDoS attacks are launched from botnets, large clusters of connected devices (e.g., cellphones, computers, routers) infected by malware that allows remote control.
How To Prevent DDoS Attack On Xbox
It’s now time to talk about why you came here.
We have listed ways to increase your network security to prevent DDOS attacks against your Xbox gaming console.
Businesses should not be dealing with a denial-of-service attack. However, it is more likely that hackers will target the entire gaming community, or the server, than a single gamer in an Xbox DOS attack.
Their leverage will increase if they can shut down large swathes of the system rather than a handful of players.
An attacker can hack into Microsoft’s system, but it isn’t much you can do.
Multi-vector attacks are more challenging to solve. It’s not something that an average gamer should worry about.
It’s best to wait, which usually doesn’t take too long.
Here are some steps you can take to help protect your Xbox against DDOS attacks.
Can Someone DDoS Me On Xbox?
If they have your IP address, someone can DDoS your Xbox. They can send you more data to your IP address, making connecting to the interInternetyour Xbox difficult.
DDoS attacks can target your actual IP address, which your Internet Service Provider provides. This is because your IP address is public, meaning that any websites and internet services you connect will have access to your IP address details.
Your IP address will be displayed to anyone you connect to when you connect to multiplayer online games. They could use this information to send large amounts of data to your Internet connection to launch DDoS attacks. It will be extremely difficult to connect to the interInternetour internet connection that is not used for data traffic.
Protecting against DDoS is easy with a VPN. The VPN server your connection is routed through may have anti-DDoS protections on its perimeter network. This could help protect you from DDoS attacks. Make sure that the VPN you choose protects against DNS leaks.
- 🚀【HIGH PERFORMANCE LAPTOP】Maypug 15.6 inch laptop uses powerful Intel Celeron N5095 processor, frequency up to 2.9GHz, no latency, and powerful and faster than normal processors on the basic frequency. Equipped with the latest pre-installed Windows 11 system which is far more safer and faster than previous Windows systems. The perfect combination of performance, power consumption, and helps your device run smoothly and reliably to handle all your tasks.
- 🚩【LARGE SORAGE SAPCE COMPUTER】Maypug Laptop is equipped with 8 GB DDR4 and 256GB high-speed SSD which lets you use it without a problem even with multi programs open. Provides huge space for efficient operation of the most complex application and multimedia. An expandable TF card slot supports maximum 512GB TF card expansion and extensive interfaces such as HDMI, 2xUSB 3.0, USB Type-C, etc. Ensures you of an enough space to create and store more of your world.
- 💻【15.6" BIG SCREEN NEWEST LAPTOP】Maypug 15.6 inch laptops with 1366*768 high resolution screen provides you with a sharp and clear text and images. The 16:9 ratio expands the vertical space of the screen, showing more content, providing a comfortable visual experience and greater efficiency when browsing web pages or documents.
- 👜【CONVENIENT AND PORTABLE DESIGN】Maypug laptops are designed with an ultra-thin case ensures of a stylish and innovative look, and excellent portability. 2cm slim body, 1.65KG lightweight. What’s more, this business and home laptop features an advanced 38000mWH rechargeable battery life of up to 8 hours. It is very convenient and portable for business trip or traveling. Suitable for daily work and play, it is the first choice for business, offices or students
- 💯【365 DAYS LIMITED WARRANTY】Maypug has strict standard for all stages of production to ensure the quality of our 2023 new laptops. All laptop computers are subjected to 200 hours of machine aging tests before shipment to make sure each frame is working flawlessly. We offer ONE-year limited warranty. Any questions about our Maypug laptops, please contact us for an easy solution or a fast replacement!
- 1.6 GHz dual-core Intel Core i5 (Turbo Boost up to 2.7 GHz) with 3 MB shared L3 cache
- 13.3-Inch (diagonal) LED-backlit Glossy Widescreen Display, 1440 x 900 resolution
- Intel HD Graphics 6000
- OS X Yosemite, Up to 12 Hours of Battery Life
- 【Intel Celeron N3060 Processor】Dell Chromebook 3180 Laptop PC, Intel Celeron N3060 Processor (Dual Core, 1.6GHz up to 2.8GHz, 4MB Cache, 6W) provides powerful processing capabilities for problem-free computing
- 【RAM and Storage】Dell 3180 Laptop Chromebook with 4GB RAM and 16GB SSD for efficient multitasking
- 【11.6 Inch Display】11.6" HD (1366x768) resolution, Intel HD Graphics, enhances graphics performance great for movies and games
- 【Chrome Operating System】Chrome OS and Chrome browser get you online in an instant and load web pages in seconds, the Dell Chromebook 3180 laptop is undoubtedly your best choice for work or study, work, leisure
- 【After-sales guarantee】This refurbished laptop has been professionally inspected, tested, and cleaned by Amazon-qualified vendors. Backed by a 90-day warranty and 90-day tech support
- 【14" HD Display】14.0-inch diagonal, HD (1366 x 768), micro-edge, BrightView. With virtually no bezel encircling the display, an ultra-wide viewing experience provides for seamless multi-monitor set-ups
- 【Processor & Graphics】Intel Celeron N4120, 4 Cores & 4 Threads, 1.10 GHz Base Frequency, Up to 2.60 GHz Burst Frequency, 4 MB Cahce, Intel UHD Graphics 600, Handle multitasking reliably with the perfect combination of performance, power consumption, and value
- 【RAM & Storage】8GB high-bandwidth DDR4 Memory (2400 MHz), Adequate high-bandwidth RAM to smoothly run multiple applications and browser tabs all at once. 64GB high-speed eMMC Storage for your office and webinar needs
- 【Ports】1 x USB 3.1 Type-C ports, 2 x USB 3.1 Type-A ports, 1 x HDMI, 1 x Headphone/Microphone Combo Jack, and there's a microSD slot
- 【Windows 11 Home in S mode】You may switch to regular windows 11: Press "Start button" bottom left of the screen; Select "Settings" icon above "power" icon;Select "Activation", then Go to Store; Select Get option under "Switch out of S mode"; Hit Install. (If you also see an "Upgrade your edition of Windows" section, be careful not to click the "Go to the Store" link that appears there.)
- 14” Diagonal HD BrightView WLED-Backlit (1366 x 768), Intel Graphics
- Intel Celeron Dual-Core Processor Up to 2.60GHz, 4GB RAM, 64GB SSD
- 1x USB Type C, 2x USB Type A, 1x SD Card Reader, 1x Headphone/Microphone
- 802.11a/b/g/n/ac (2x2) Wi-Fi and Bluetooth, HP Webcam with Integrated Digital Microphone
- Windows 11 OS
- Windows 10.
- System ram type, ddr3_sdram
- Memory storage capacity, 4.0
- Package Weight, 3.765 kilograms
- 【Powerful Intel N100 processor】 Laptop is equipped with a powerful 12th generation Intel N100 processor, with a main frequency of up to 3.4GHz, 4 cores and 4 threads, made with Intel 7nm process, running your work tasks and loading applications smoothly, equipped with a 38WH Li-polymer battery and a superb cooling system, power optimization is more energy efficient, more performance.
- 【Large Capacity Storage】 Laptops computer is equipped with 16GB of RAM, 512GB of high-speed SSD, and up to 256GB of TF card expansion support, providing superb storage space for complex applications as well as large amounts of streaming media. DDR5 achieves a 4800Mhz main frequency for smoother operation, and the traditional laptop is then paired with a separate numeric keypad and an extra-large touchpad with an ergonomic keyboard The design allows you to operate more convenient, improve your work efficiency.
- 【Large Screen Computer with 16:10 Aspect Ratio】 Traditional laptop computer is equipped with a 16-inch FHD (1920x1200) IPS display, 93% ultra-high screen-to-body ratio, built-in Intel UHD graphics, FHD anti-glare screen effectively reduces the interference of the external light, support for 4K video @ 60Hz, ultra-high-definition display lets you have an immersive experience to watch movies, videos, etc., suitable for students, teachers, and Suitable for students, teachers and office workers.
- 【Dual-band WiFi and Four Stereo Speakers】Computer laptop is equipped with 2.4G+5G WiFi/BT4.0, adapted to 802.11b/g/n + ac band, fast connection to the network and access to the device, coupled with four stereo speakers to efficiently output the audio, the front 1.0 MP camera, the video call is more clear, enjoy the network world!
- 【External Ports】Lap top comes with ports USB3.0*2, 3.5mm headphone jack*1, Type-C connector, DC charging port*1, Mini HDMI*1, TF expansion port*1, which can be connected to multiple devices to meet the needs of your need to access multiple devices. Jumper laptop warranty is one year, please feel free to contact us if you have any questions.
- READY FOR ANYWHERE – With its thin and light design, 6.5 mm micro-edge bezel display, and 79% screen-to-body ratio, you’ll take this PC anywhere while you see and do more of what you love (1)
- MORE SCREEN, MORE FUN – With virtually no bezel encircling the screen, you’ll enjoy every bit of detail on this 14-inch HD (1366 x 768) display (2)
- ALL-DAY PERFORMANCE – Tackle your busiest days with the dual-core, Intel Celeron N4020—the perfect processor for performance, power consumption, and value (3)
- 4K READY – Smoothly stream 4K content and play your favorite next-gen games with Intel UHD Graphics 600 (4) (5)
- STORAGE AND MEMORY – An embedded multimedia card provides reliable flash-based, 64 GB of storage while 4 GB of RAM expands your bandwidth and boosts your performance (6)
- Intel Celeron N Processor Up to 2.75GHz, 4GB DDR4, 64GB SSD
- 13.8" Brightview HD(1366x768) IPS Display, Intel UHD Graphics
- 1x USB Type C, 2x USB Type A, 1x HDMI, 1x Headphone/Microphone Combo Jack
- Super-Fast WiFi and Bluetooth Combo, Integrated Webcam
- Windows 11 OS, AC Charger Included, Pastel Pink
- 18 Months Warranty
- Get the most out of your laptop with Intel premium high performance Core i5-2540M processor at 2.60 GHz.
- Store up to 320GB of data and access it even quicker with 8GB of Ram.
- Enjoy working on this light 4 pound device anywhere with it's easy on the eyes 14" display at 1366 x 768 resolution.
What the Law Says
Computer Misuse Act 1990 makes it unlawful to intentionally interfere with the operation of a computer or prevent or hinder access from a program/data on a machine unless you have been authorized to do so.
This means that distributed denial of service and similar attacks are considered criminal under UK law.
It is also illegal to supply, obtain, or make stresser or booter services to facilitate DDoS attacks.
This law is necessary because DDoS attacks, the use of booter or stresser services, and DDoS attacks can cause serious harm to individuals, businesses, and organizations.




![41T6htXy55L. SL160 65 $15 Xbox Gift Card [Digital Code]](https://m.media-amazon.com/images/I/41T6htXy55L._SL160_.jpg)





































